BYOD Gains Traction as Employees Demand Access from Mobile Devices
Dan Hebert is a former senior technical editor for Control, Control Design and Industrial Networking.
What if your company told you that you no longer were allowed to make business-related calls from your smartphone, but instead had to use a company-issued phone so that all communications could be closely monitored and controlled? How would that sit?
Consider that in the near future, employees of industrial firms might feel the same way about being denied access from their smartphones and tablets to enterprise and operating information that's readily accessible from their work computers.
Besides meeting employee expectations, there are many other benefits to bring[ing] your own device (BYOD).
Security Issues
Before discussing BYOD benefits, let's look at the security challenges to integrate BYOD into the enterprise, as they are the main impediment to widespread adoption.
BYOD is an area where IT must interface with many other departments within a company to ensure proper implementation of security policies. "Our view of BYOD is not focused on mobile device management, but rather on mobile application management (MAM)," says Paul Stamas, CIO and vice president of information technology at paper manufacturer Mohawk. "MAM describes software and services responsible for provisioning and controlling access to internally developed and commercially available applications used in business settings on both company-provided devices and BYODs." (For more on how Mohawk uses BYOD, see the sidebar "Mohawk Buys into BYOD.")
Michael Hake is facilities technician at an electronics manufacturer in Bohemia, N.Y. His company uses Opto 22's groov and four Android and two Apple smartphones to monitor and control its facilities.Hake says it was "very plug and play."
Read more here.
"BYOD and security aren't necessarily at odds," says Richard Clark, security engineer at Indusoft. "Most BYOD concerns are centered on the security of the device, but the real issue is where and how such devices will be allowed.
"I bring my own OSX Apple MacBook Pro notebook to work. The issue is not so much whether to allow it on the network, but how to handle it when it is."
Clark says the MacBook Pro is virtually transparent on the network, but has several client applications, some running Windows operating systems, that are authenticated as individual machines on the network. This, he adds, is the security model that must be used when accepting any other device within an area or location.
"Security needs to be managed in some of the same ways all other corporate network access is managed," says Ben Orchard, Opto 22's applications engineer. "First decide who gets access to what. Then look at three levels of security: secure the device, secure the network and secure the application."
Also Read: Is BYOD Inevitable in the Manufacturing Space?
Mohawk Paper in Cohoes, N.Y., has a history of adapting to new ideas and technologies. Mohawk was the first U.S. paper mill to match 100% of its electricity with renewable wind power and the first U.S. premium paper mill to shift toward carbon-neutral production. So BYOD is not an unexpected step for them. Read more here.
Securing the device with a PIN, swipe pattern or other method is fairly simple. To secure the network, Orchard says, use IT best practices for keeping data safe and allow only authorized users. "Segment your control network and critical equipment," he advises. "If the user is required to access the plant or process after hours, then use a VPN."
Next, secure the device's remote access application, which will either be a browser or an app. "The application itself should be password protected, first to open and then for levels of access," Orchard says. "A worker's username should allow only him or her access to pertinent parts reflecting work requirements. Perhaps some users need to monitor equipment, but not control it; their screens would not have any buttons or input methods. The application should adjust to higher levels of username/password, and allow control only to those who require it."
Clark notes that smartphone problems are just beginning and could become similar to current issues with company-issued laptops, which are often unknowingly infected at home, then brought back to work where they spread the virus. "Most recently this issue has spread to mobile, iPad and smartphone devicess. While these devices currently can't carry an infection capable of spreading within a normal corporate authenticated environment, it's clear that at some point they might be able to."
He suggests tighter security measures. "Device authentication can provide information about what it is and where it is—and presumably where the user is," he suggests. "Using other proximity authentication, such as Bluetooth and bar-code readers, will allow location authentication of users and devices within proximity to allowed areas or machinery. Once the person leaves the area, the content for that area no longer will be available. Another advantage of knowing where devices and users are located is that intelligent alarming can occur, which will direct alarms to the nearest appropriate people."
Monitoring Versus Control
- It's less expensive than providing employees with corporate devices
- It provides remote access from anywhere
- It costs less than plant-floor HMIs
- It costs less than buying site licenses for remote PCs
- Many vendors offer free or low-cost device access
- Employees don't have to carry multiple devices
- Employees are more productive using familiar devices
- Companies often subsidizes part of employees' device costs
- It Improves employee morale
Not many people oppose BYOD for monitoring production processes, but there are myriad concerns when it comes to using personal devices to make changes to an operating facility.
One end user, requesting anonymity, at a major Midwest refiner says, "I don't see our company or any other oil company offering control from a personal device. If something bad ever happened we would get pilloried. We're downright paranoid about external connections to the control system to the point where even serial Modbus connections get closely scrutinized. I personally consider this a good thing. Let the companies that don't make stuff that burns and explodes figure it all out before we wade in." Monitoring via a personal device is OK, he adds.
Diane Trentini, vice president at Optimation Technology, a system integrator in Rush, N.Y., hasn't seen any demand for control using personal devices. "We've had small projects in which process or production information such as status updates and alarms are sent to a personal mobile device," he says. "There are also Web-based displays of process data that can be accessed by a personal mobile device. But to date, we've not implemented mission-critical controls on personal devices."
- Employee owns device and therefore has admin rights
- Procedures required to disable device in event of theft or employee dismissal
- Different devices have different procedures for invoking security
- Device usage must be restricted based on employee’s role, location of device and other factors
- Hackers may be able to monitor device traffic
- Malicious software is starting to invade smartphones and tablets
- The the device hardware, remote access software and the network all must be secured
Lou Bertha, an engineer at RDI Controls, a system integrator in Lower Burrell, Pa., believes BYOD for control is OK if used judiciously. "There are advantages to being able to access plant information via employees' personal devices," he says. "A smartphone or tablet can be great for troubleshooting, remote diagnostics or monitoring a system while away from the control room, etc. This type of remote access could be set up on a personal device without any issues."
But for control, care must taken. "Depending on the process, the ability to modify critical processes might or might not be warranted," he says. "Each process—power generation, water treatment, widget making, etc.—has its own conditions on what's critical and what's not. You might not want to give the ability to trip the entire plant via a smartphone, but would want to allow people to turn motors on and off via personal devices."
With many systems, the capability to control with a personal device is readily available, but not everyone uses it. "We use mobile applications to monitor our processes, not to control them," Stamas says. "The system has the capability, but we just haven't had the need to make process changes remotely via mobile applications."
BYOD in the Real World
Monitoring with an employee-owned device is catching on much faster than control. One reason might be that a smartphone supplied by the employee is much less expensive than installing HMIs throughout a plant. Those additional HMIs often come with expensive site licenses and require ongoing support, such as periodic software updates. With a personal device, access is via apps and web browsers, which are updated by the suppliers, usually at much lower costs.
John Cusimano, director of industrial cybersecurity at aeSolutions, a system integrator in Greenville, S.C., recently worked with a client in the water/wastewater sector who replaced hard-wired operator interface panels with company-provided portable devices. The devices connected to the control system via a short-range 802.11 wireless-access point.
"The hard-wired panels were obsolete, and they had trouble maintaining them," Cusimano says. "They had about 10 of them in specific locations throughout the plant. They could have replaced them with current models, but it was less expensive to purchase a few general-purpose portable devices. The operators and techs needed access to the information when they were on the floor, and it made more sense for them to have access anywhere."
Employees throughout the industrial enterprise want to remotely access all types of corporate data. This BYOD trend is here to stay, and IT departments need to provide convenient yet secure methods to access data through smartphones and tablets.
"The use of enterprise file sync-and-share applications has seen tremendous growth in the past year," notes Jeetu Patel, general manager for EMC Syncplicity. Syncplicity is a software platform for secure data and file sharing from the enterprise to mobile and other devices.
Read more here.
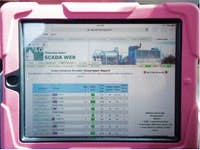
BYOD monitoring is accepted by most all operations personnel, but not necessarily IT. "I wanted to use my own iPad for monitoring a natural gas pipeline, but it took a while before I was finally allowed access to the company Wi-Fi and VPN," says Dennis Brown, senior measurement engineer at Cherokee Basin Pipeline in Independence, Kan. (Figure 1). "Historically, there's been a policy of no access for personal devices, with security always cited as the primary reason."
Here to Stay
Although this article focused on the use of personal devices to monitor and control production processes, BYOD is also 4idely used to view and make changes to industrial operations in many other areas of the enterprise from accounting to logistics to sales and marketing. (The "Sharing and Syncing Data Using BYOD" sidebar discusses methods to provide access to these areas by integrating devices into the entire enterprise via hybrid clouds and other tools.)
BYOD is a growing trend, but some companies are still afraid of it. Perhaps an interim solution would be for a company to supply smartphones or tablets to employees. That way, the company's IT department could install all the necessary procedures, access controls and other requirements needed to ensure a safe and secure working environment. Once everything works to the company's satisfaction, it then could transition to a BYOD policy.
Figure 1: Dennis Brown of Dart Oil and Gas uses his own iPad to monitor company operations via the company Wi-Fi and VPN.
On the other hand, your company could get forced into BYOD, and sooner than you think. Stamas explains how Mowhawk's system got launched: "Our BYOD solution was requested by the president of the paper division. He wanted real-time visibility into the state of plant applications for himself and his staff 24/7. He told me he wanted to be able to wake up in the middle of the night and check the status of his operations in minutes."
So when the president of your company learns that such things are possible with a smartphone, you might get the same request.
Not many people oppose using personal devices for monitoring production processes, but there are myriad concerns when it comes to using them to make changes to an operating facility.
"Our view of BYOD seeks to ensure that a specific enterprise footprint is provided on a personally owned or a company-provided device, with either limited to certain applications and data. In our case, that's manufacturing applications and data."