As operations technology (OT) and information technology (IT) converge, industrial organizations have started to reinforce their network security and are taking cybersecurity precautions to protect their operations.
Critical infrastructure and manufacturing facilities are more likely to be targeted by cyberattacks, as companies could need to halt their production lines for more than one day due to a cyberattack.
In addition to incurring financial losses, a company’s reputation can be damaged when it’s hit by a cyberattack. Companies are being targeted by ransomware attacks, and some are being targeted, despite having taken precautionary measures. These attacks demonstrate the risk of an interconnected world, and no organization is immune from cyberattack.
Chief security officers, specifically chief information security officers, want to learn more about OT environments and how to effectively implement cybersecurity measures without disrupting industrial operations. There are many approaches and architectures that must be considered.
Defense-in-depth and zero-trust approaches
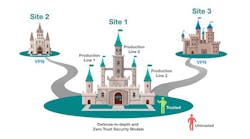
The initial focus of zero-trust architecture, as stated in the NIST Special Publication 800-207, is to only grant the minimal access privileges to those who need to operate on the network. This will prevent the situation whereby someone has a legitimate reason to access the network, but they are unnecessarily given unrestricted access to parts of the network that they do not require access to, which increases the chances of a cybersecurity breach occurring.
The defense-in-depth approach contains multiple layers of security protection to reinforce network security for industrial operations. The rationale behind this is that you’ll have a second chance to protect zones and conduits if the first layer of protection fails. According to the IEC 62443 cybersecurity standard, it is necessary to start this process by partitioning areas based on the levels of protection required.
Also read: Defense-in-depth leads cyber strategy for OT security
Each partition is called a zone, and all the communication devices within it share the same security level, which means they all have the same level of protection. If you want to enhance security even further, it is possible to place a zone inside another zone with additional security measures.
By combining the two approaches that we have just considered, you can build well-defended industrial operations with layers of protection as the foundation and then add further protection by adding the zero-trust mechanism to ensure access is restricted to only those who need to access certain areas of the network (Figure 1). After considering these two approaches, it is clear there is no silver bullet for cybersecurity and there are multiple angles that must be considered to ensure your network is secure.
Enhance cybersecurity awareness
It’s important to enhance cybersecurity awareness across different departments and make sure all team members have the same mindset regarding cybersecurity. Employees should be encouraged to understand the benefits of the following technical security requirements, as this will increase the chances that the guidelines are adhered to.
This requires:
- coordinated security responses, as well as network monitoring and management
- an assumption that all devices and networks will be compromised
- ensuring there are robust recovery-and-response processes.
Strong authentication for users and devices
One unfortunate scenario that is often seen on industrial networks is when user credentials are compromised. For networks that do not utilize the zero-trust principle, a user’s credentials might be all a malicious actor needs to gain access to the network. However, for a network that utilizes zero-trust architecture, a malicious actor requires not only device access control but also user authentication and authorization. On top of that, it is suggested to utilize trust lists for granular control of your network.
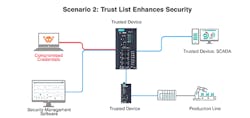
Device access control: By using trust lists, rate control and failure logout, network devices only allow access from trusted devices that are equipped with the secure boot function and prevent excessive attempts such as brute-force attacks.
Figure 2: If organizations hope to reinforce security, trust lists can be a good way to control network traffic.
User authentication and authorization: By verifying the user’s credentials when logging on to devices, network devices will log all user access attempts and provide the lowest level of privileges based on the role of the user.
Trust lists: If organizations hope to reinforce security, trust lists can be a good way to control network traffic (Figure 2). One common practice is to create a trust list for IP addresses and service ports and leverage deep packet inspection technology to granularly control the network with features such as read or write privileges.
Segmentation for defense-in-depth
Remote connections are an essential part of industrial control systems, which must be managed effectively. At the same time, insider threats still pose a risk to the network. Steps must be taken to ensure that the risks posed by both scenarios are minimized. Appropriate network segmentation can prevent malicious actors from accessing the entire network if they compromise remote connections or if there is an insider threat to the system; it will stop the person gaining access to the entire network (Figure 3).
Figure 3: Appropriate network segmentation can prevent malicious actors from accessing the entire network if they compromise remote connections or if there is an insider threat to the system.
Network segmentation: Segmented networks can prevent malicious actors from moving laterally across networks. Oftentimes, organizations deploy firewalls between the IT and OT networks to create high-level network segmentation. However, once a malicious actor compromises user credentials, it is very likely that the person can access devices and the networks in the OT network, if the network is not segmented appropriately. There are several approaches that can be taken to help achieve network segmentation including deploying firewalls. One of the benefits of using a firewall is that it helps administrators establish zones in the network to only allow permitted traffic to transfer from one zone to another. Furthermore, security policies and rules, such as IP addresses and only authorizing ports that are in use, will help segment the network into smaller, easier-to-manage sections to ensure only necessary traffic is allowed on the network.
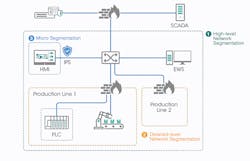
Micro-segmentation: One of the many critical assets in industrial control systems are motion controllers. When critical assets such as these are compromised, it may bring production to a halt or even cause damage that could put people’s safety at risk. Therefore, asset owners can deploy industrial intrusion prevention systems to contain cyberattacks within certain zones and protect critical assets (Figure 4).
In addition, continuous monitoring for anomalous activity by users and devices on networks can help reduce the spread of the attack and allow personnel to restore the network more quickly.
Figure 4: Industrial intrusion prevention systems can be deployed to contain cyberattacks within certain zones and protect critical assets.
Felipe Sabino Costa is an ISA/IEC-62443 industrial cybersecurity instructor and ISA District 4, Brazil, cybersecurity director for the International Society of Automation. He is also a LATAM Industrial Cybersecurity expert at Moxa. Contact him at [email protected].
Continue Reading

Leaders relevant to this article: