What are the 7 layers of the OSI model?
I have been working with controls and automation for more than 20 years. I’ve witnessed the transition of control systems from primarily private, serial, mostly proprietary networks to more Ethernet-based networks.
Controls engineers need to gain more knowledge involving these types of systems. The Open Systems Interconnection (OSI) model is an important topic, as it relates to industrial control system (ICS) networking.
Get your subscription to Control Design’s daily newsletter.
Let’s say we want to communicate a message to someone. What two fundamental elements are needed for that to take place? The first would be the format, and the second would be the media. What do I mean by that?
The format would be the specific language with which we are going to communicate—for example, American English. There are many languages, or formats, of communication, that can be used, but, unless there is a common, agreed-upon way to communicate, the message will never be understood.
The media would be the avenue through which we would deliver this message. A web browser, for instance, displays content. There are many avenues we can use to communicate, such as a phone call, text message, email or in-person communication. This, too, needs to be agreed upon. We may both intend to communicate in English, but, if I am expecting a phone call and an email is sent instead, it might be a while before I realize I have a message. For us to be able to communicate, we would have to agree on both a format and media.
Industrial control system networks are similar. We just use different words to describe it.
Like format and media, we have protocols and standards that we use to help broker communication between devices. Think of protocols kind of like a specific language and standards as an agreed-upon way of formatting that communication.
When we want to send an email to someone, first we open an email application, like Microsoft Outlook, on our laptop. Next we click on “new message” icon to create an email. Then we put in an email address to designate the recipient. We fill out the subject line and body of the email. After we have proofread the message, we hit the send icon, and away it goes.
What about the person on the other side? That person gets a notification. After opening the email application, the person sees the unread email, clicks on it and reads it. This message went from one computer to another. Was it magic?
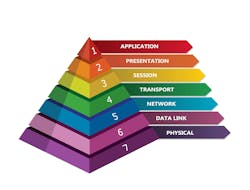
7 layers of the OSI model
To help see how that worked, let’s take look at the OSI model, which describes seven layers that computer systems use to communicate over a network.
Starting at Layer 7, the highest-level layer and moving down, you have:
- application layer
- presentation layer
- session layer
- transport layer
- network layer
- data link layer
- physical layer.
In our email example, the message starts in Layer 7 of the source machine, and then it moves all the way down through the layers to Layer 1. Next, the message is transmitted to the destination machine. Finally, the message goes from Layer 1 of the destination machine up to Layer 7.
OSI layers 4 through 7 are always implemented in the software, while layers 2 through 3 are a combination of hardware and software. Layer 1 is almost completely hardware.
Layers 1, 2 and 3 are network support layers and happen to be the layers we are most concerned about from an automation network standpoint. They deal with physical aspects of moving data, such as electrical specifications, physical connections, physical addresses, transport time and reliability from one device to another. Layer 4 ensures reliable data transmission. Not all applications need to use all seven layers. The lower three layers are sufficient for most applications.
Application layer
At the very top of the OSI reference model stack, we find the application layer, which is implemented by the network applications. These applications produce the data that is to be transferred over the network. This layer also serves as a window for the application services to access the network and for displaying the received information to the user.
The hardware associated with this layer is almost always the computer, and the information is communicated as data. For our email example, Microsoft Outlook operates in this layer.
Presentation layer
The presentation layer is also called the translation or syntax layer. The data from the application layer is extracted here and manipulated as needed to conform to the required format to transmit over the network.
The hardware associated with this layer is almost always the computer and the implementation of this layer is done by network application software, such as web browsers and email clients. The information is communicated as data.
For our email example, the data gets converted into American Standard Code for Information Interchange (ASCII) format in this layer, and likely is encrypted using secure sockets layer (SSL).
Session layer
The session layer is responsible for establishment of connection, maintenance of sessions, authentication and ensuring security.
The hardware associated with this layer is almost always the computer and the implementation of this layer is done by network application software, such as web browsers and email clients. The information is communicated as data. For our email example, remote procedure call (RPC) is likely being used in this layer.
Transport layer
The transport layer provides services to the application layer and takes services from the network layer. It is responsible for the end-to-end delivery of the complete message. The transport layer also provides the acknowledgment of the successful data transmission and re-transmits the data if an error is found.
The hardware associated with this layer includes load balancers and firewalls, and the communicated information is broken down into segments. For our email example, transmission control protocol (TCP) is likely being used in this layer.
Network layer
The network layer works for the transmission of data from one host to the other located in different networks (internetworking). It also takes care of packet routing, which is the selection of the shortest path to transmit the packet, from the number of routes available. To identify each device on the internetwork uniquely, the network layer defines an addressing scheme. The sender’s and receiver’s internet protocol (IP) addresses are placed in the header by the network layer.
The hardware associated with this layer includes routers, and the information is communicated in packets. For our email example, IP is likely being used in this layer.
Data link layer
The data link layer is responsible for the node-to-node delivery of the message. The main function of this layer is to make sure data transfer is error-free from one node to another, over the physical layer. When a packet arrives in a network, it is the responsibility of the data link layer (DLL) to transmit it to the host using its media access control (MAC) address.
The hardware associated with this layer includes switches, and information communicated is frames. For our email example, Ethernet is likely being used in this layer.
Physical layer
The lowest layer of the OSI reference model is the physical layer. It is responsible for the actual physical connection between the devices. It controls the transmitting of the individual bits from one node to the next. When receiving data, this layer will get the signal received and convert it into 0s and 1s and send them to the data link layer, which will put the frame back together.
The hardware associated with this layer includes hubs, repeaters, modems and cables. Cables come in many different varieties. The information communicated is bits. For our email example, a combination of fiber optics, copper and Wi-Fi are likely being used in this layer.
Recap
To review, the application, presentation, and session layers are all primarily dealing with data. When you get to the transport layer, the data is broken into segments. In the network layer, those segments are broken into packets. In the data link layer, those packets are broken into frames, and, in the physical layer, those frames are converted to a binary transmission.
About the Author
Patrick Bunn
Bunn Automation Consulting
Patrick Bunn, owner of Bunn Automation Consulting in Birmingham, Alabama, will be discussing industrial network protocols, the OSI model and how to use Wireshark software for troubleshooting in his presentation, ICS Networking, at OT SCADA Con 2025 in Houston. Bunn will speak at the event on July 24 at 3 pm. Use the code PATRICK to receive 15% off your registration fee for OT SCADA Con 2025. You can also contact Bunn at [email protected].