We're sold on the value of remote diagnostics via web browser to troubleshoot customer problems without travel. There's a lot of resistance from some about network vulnerability. What's my argument to this? A lot of it seems subjective.
—From December '10 Control Design
ANSWERS
Keeping Control Is Key
In an age of malware, hackers, viruses and WikiLeaks, network security is on the top of everyone's mind. Most companies of any size have their networks locked down tighter than a drum. But to benefit from remote diagnostics, networks need to be opened up, and this results in some very legitimate concerns.
Even with a relationship founded on trust, when a factory depends heavily on external support, the risks associated with network security must be taken seriously.
Today, the best practice for allowing secure remote access of a company network is a virtual private network (VPN), but even VPN usage creates issues.
Generally, control of the VPN lies in the hands of the customer IT group. They face three challenges when setting up VPN access with current solutions. First, granting rights to and administering external users is very tricky (not to say uncomfortable) and time-consuming.
Second is lack of traceability; because of the inherent properties of VPN, the IT group has almost no way to understand how, when and by whom the connection is used.
Third, the need to open firewall ports to allow external access of equipment goes against corporate IT policies. When the customer network has not been segmented, a VPN connection provides access to the whole factory network—very dangerous.
So, what are the other options? Provide an approach that empowers the IT group to fully manage and control the VPN connections to their machines while simultaneously providing remote experts with a secure and reliable connection for efficient troubleshooting and diagnostic activities. Cloud-based services, for example, can enable the administrator to easily manage access control, allowing VPN connection to only selected machines and equipment over the existing IT infrastructure. The IT group suddenly enjoys a far better position to manage secure access to its networks.
ABB (www.abb.com) uses our company's technology globally to provide remote diagnostics for its industrial robot applications, and it allows customers to significantly reduce the need for onsite calls.
Dominique Blanc, Engineer,
eWon, www.ewon.us
Isolate the Network
Although it's true that remote diagnostics can open up a network to external threats, the implementation of a common network architecture can allow you access to the information you need and keep your customer's network safe.
There are two main network vulnerabilities that come to mind: gaining access to the customer's internal network, and theft of proprietary data about the state of its machines by a third party.
Fortunately, there is a network architecture commonly used by IT professionals that can allow only your company access to the customer's data and still keep you out of the rest of its network.
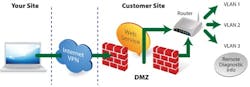
The first key to this is for the customer to set up virtual LANs (VLANs) on its internal network (see Figure). VLAN is a network standard, also referred to as IEEE 802.1Q, that segments your network into smaller networks, none of which can communicate with each other without permission from a central router. By placing all of the data that you would need external access to on one VLAN (the monitoring equipment and the web service), your customer can provide you access to everything you need without compromising its network integrity.
This idea of data isolation also can be taken beyond VLANs. The web service that provides data to the browser can be placed in a network demilitarized zone (DMZ), a section of network that is open to external communication, but isolated from the rest of the network by a second firewall. Any threats that make it through the first firewall via the web service still have no access to the rest of the network.
Everything mentioned has been about isolating internal components of the customer's network. There is still the problem of publishing data to an external web browser. Instead, the customer could forego that vulnerability entirely and publish the web service on its internal network only. You could then be granted access to the same VLAN as this internal web service through a virtual private network (VPN). A VPN treats a remote network as if it's on an internal network, while providing two-way authentication and protection against anything the Internet might throw at you.
So, by isolating the customer's network and allowing you only limited access to certain portions of it through VLANs, in addition to protecting its network from external threats through VPN, your customer should have limited realistic concerns about network vulnerability.
Doug Farrell, Product Engineer,
National Instruments, www.ni.com
Keeping It in Motion
While supporting customers of our motion controllers, we frequently connect remotely to their PCs. This is tremendously useful for tuning unusually difficult motion control applications.
Basic tuning involves repeatedly moving the axis and viewing the plots of the motion to determine what parameter to adjust. Tuning a difficult system additionally requires a level of knowledge of the control algorithms that can be gained only through years of experience. Remotely connecting to a PC allows us to provide the customer with that expertise on site with no travel expenses, and no time delay.
Customers with technical problems are universally interested in enabling us to help them resolve their issues in any way possible, and rarely do we encounter a customer unable to connect because of security issues, although poor bandwidth occasionally prevents connection.
We use well-known and proven products such as GoToMeeting or WebEx—perhaps that's one reason why security issues never come up. The only case was an instance with the U.S. military, whose electronic security at certain locations is too tight to even allow downloading motion control software from our website.
Rather, because we offer free technical support, the greater issue is the need to limit the use of the remote connection to avoid crossing the line from providing technical assistance to actually performing the machine integration.
A recent example of successful remote diagnostics involved the installation in Brazil of a sheet metal forming machine designed by Scott Technology of New Zealand. Scott Technology easily tuned 11 hydraulic axes with Delta's auto-tuning feature. However, one hydraulic cylinder was not controllable at the required speeds and accelerations, despite following the recommendations of Delta technical support. We connected remotely to the installation engineer's laptop in Brazil, and performed the tuning from our headquarters in Battle Ground, Wash.
After moving the axis several times, we determined that the cylinder was quite undersized for the load. Delta's controllers include advanced algorithms capable of controlling undersized cylinders, but the question is, of course, how small the cylinder can be and still maintain control.
After several hours of challenging tuning, which resulted in several hundred of plots of motion, control within the required tolerance was achieved, although we expressed concern that any changes in the system, such as oil temperature, might cause instability. Indeed, the next day, with a cold machine, the cylinder began oscillating during motion.
With the system knowledge we gained during the tuning process, we recommended increasing the cylinder size. From the plots obtained during tuning, we were able to analyze the system and the required motion, and suggest an appropriate cylinder size. The customer installed the new cylinder and the axis completed its tuning using the controller's auto-tuning feature.
Jacob Paso, Electrical Engineer,
Delta Computer Systems,
www.deltamotion.com
Never Completely Safe
The answer to that question is subjective and opinionated. Technically speaking, you do not want any control entity connected in any way to the Internet. Last time I checked the government standard was back in 2001, and it stated the only safe connection is one that is not connected.
Do you really want a nuclear cooling system control connected in any way to the Internet? All it would take is a math/computer whiz to hack it.
That being said, there are many ways to enable security measures. I have a lot of ideas, many of which I have done in the past, none of which are 100% secure. The fact is if you are connected to the Internet you are not 100% secure.
One method is to use a VPN connection, putting the HMI behind a firewall as a common scenario. If read-only is acceptable, install a video capture card on Computer 1, which is connected to the VPN. Make Computer 2 the HMI. Connect Computer 2's video output to the video capture card of Computer 1. This absolutely ensures total security for control. The only thing that can be compromised is the video capture feed.
Kevin Romer, Application Engineer,
Advantech, www.advantech.com
Continue Reading

Leaders relevant to this article: