Wireless Security, Standards Are Still Hurdles to Potential Users
Ian Verhappen is an ISA Fellow, Certified Automation Professional and a recognized authority on industrial communications technologies with 25+ years' experience. You can contact him at [email protected], via his blog at community.controlglobal.com/kanduski, or check out his Google+ profile.
]Industrial wireless networks are the "next big thing" for industrial automation and industrial networking in particular. However as with all new technology, the adoption rate often lags both the level of coverage in the press and, of course, the number of purchase orders that companies developing the technology need to recover their investment, at least in the short term. Experience has shown that any new technology in the industrial arena follows the traditional chasm model of early adopters and major companies that install small-scale pilot plants or test systems to see how it works and understand the technology. The results of these small-scale tests then form the basis of corporate standards and practices for larger-scale rollout and adoption of the new technology.
A recent study by ON World confirms that this trend is being repeated for industrial wireless. As a result, it is unlikely that large-scale adoption of industrial wireless will take place until the middle of this decade. If the challenges of security and standards are not addressed, this date likely will move farther into the future.
So just what is the current situation on these two important considerations?
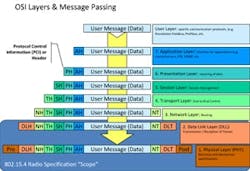
Figure 1: The OSI seven-layer model is the basis for design of all industrial protocols.
All industrial protocols use the OSI seven-layer model as the basis for design, and the 802.15.4 radios on which the industrial wireless protocols are based use the lower two layers — physical and data link — of the model (Figure 1). This makes it possible for the various protocols to use the same basic radio while all being unique, based on how to define the network through user layers to meet the requirements of target vertical industries.
Security
Fortunately, the engineers designing the industrial wireless communications protocols were aware of the concerns and impending regulations such as the North American Electric Reliability Council Critical Infrastructure Protection (NERC CIP) standards that deal with security of the electrical grid and include cybersecurity as a key component of the nine published documents, and the ISA-99 standards themselves. In fact, part of the mandate for the ISA-100 committee is that it work with the ISA-99 committee on this aspect of the standard development and ISA-84 for safety-related parts of the documents as well.
The developers of the industrial wireless standards incorporate a variety of security features in the protocols. Message encryption is a commonly used tool to maintain data integrity and prevent deliberate or inadvertent interception of the data between two nodes on a network. The process automation wireless protocols include industry-standard, 128-bit AES encryption, unique encryption keys for each message, and have the access point provide rotating encryption keys as part of its responsibilities when new devices attempt/request permission to join the network.
Other features incorporated into industrial wireless standards include data integrity — data is not corrupted — and device authentication — the device really is who it claims to be — two of the three pillars of cybersecurity, the third being authority — the device has sufficient security privileges to make the change being requested.
A channel-hopping feature makes it more difficult for a device that is not part of the network — no access to the hopping key — to be able know at which frequency the next transmission will take place.
Multiple levels of security keys for access by different individuals with different responsibilities are another important feature. This reinforces the concept of authority, that third pillar of security.
Adjustable transmit-power levels let the user manage signal spillage beyond the boundary of the plant environment. If the radio signals do not go beyond the edge of a facility, it becomes much more difficult for someone to either steal information or capture enough data packets to be able to decipher and compromise the data package format.
Wireless networks have security servers similar to RADIUS servers in the office environment, and the network manager records every attempt to join the network. By keeping track of the attempts, indication of failed access attempts can provide a measure of how vigorously someone is attempting to compromise your network.
ISA100
The ISA100.11a protocol incorporates two important characteristics to help deal with coexistence.
Slow hopping permits the radio to move from channel to channel, looking for one that is not busy. Unlike other protocols, ISA100.11a can return to a previously busy channel to determine if it might now be available.
Other approaches use "black listing," whereby a channel is declared off-limits, or not available, and is never revisited. ISA100.11a embraces "white listing" that indicates channels that have been found to be particularly good for the needs of the network. To enable "white-listing," the ISA-100 standard modifies the 802.15.4 data link layer to increase signal reliability in the industrial environment.
Any protocol compliant with the full specification of IEEE 802.15.4 must yield to IEEE 802.11 as a requirement of claiming compatibility with the standard. ISA100.11a is not fully IEEE 802.15.4-compliant. IEEE 802.15.4 radios are used since they are inexpensive and available, but the team has implemented a different media access control (MAC) protocol to improve the reliability and reduce the coexistence issues associated with the 802 family.
Profiles in ISA100.11a allow users to select the amount of protection desired. A key feature of ISA100.11a is the key distribution approach. ISA100.11a allows redistribution of keys in real time so the theft of a device does not give the thief access to a key that will be used forever more in the plant. This redistribution is done over the air so the user maintenance staff is not troubled with touching every device being rekeyed. Other protocols in the marketplace use a key entered during manufacture so it can't be changed or one that can only be changed with an out-of-band signal from a handheld unit that must touch every node in the network. The end users on the ISA100 committee were very vocal about this feature and agreed to the momentary risk of the over-the-air transmission as the best compromise available in this situation.
ISA100.11a uses three different approaches to optimize power use. Dust Network's time synchronized mesh protocol (TSMP), under a standard access agreement, allows nodes in the mesh to wake up only when there are messages to be forwarded. Other mesh protocols require the intermediate nodes to be powered full-time.
ISA100.11a allows end nodes to be completely non-routing. This provides for the peel-and-stick wireless sensors envisioned for some simple installations. Since these nodes are non-routing, they don't need to wake up to pass messages around the mesh and they don't have to maintain a complicated routing table, so they can be implemented with much simpler electronics and reduced memory.
The ISA100.11a specification allows for programmable power levels for the output radio. This approach can be used along with the received signal strength indicator (RSSI) to optimize radio transmission power for the instantaneous needs in the network. This feature also can have security implications since the range of the RF signal can be tailored with the power of the transmission.
WirelessHART
Techniques such as direct sequence spread spectrum (DSSS) technology (coding diversity) and adjustable transmission power (power diversity) also help WirelessHART provide reliable communication even in the midst of other wireless networks. WirelessHART also uses time-synchronized communication — time diversity — to minimize the potential for collisions by blacking out channels being used by other devices and networks. All WirelessHART device-to-device communication is done in a pre-scheduled time window, which enables collision-free messaging. In addition, each message has a defined priority to ensure appropriate quality-of-service (QoS) delivery. Fixed time slots also enable the network manager to create and manage the network for any application without user intervention.
WIA-PA in China
Wireless network for industrial automation — process automation (WIA-PA) based on IEEE 802.15.4 is proposed by Shenyang Institute of Automation, Chinese Academy of Sciences. WIA-PA network supports a hierarchical network topology that is a hybrid of star and mesh. The first level of the network is a mesh topology where routing devices and gateway devices are deployed. The second level uses a star topology where routing devices and field/handheld devices are connected. Like other protocols, the WIA-PA protocol stack is based on the ISO/OSI seven-layer reference model and only defines the data link sub-layer (DLSL), network layer (NL) and application layer (AL). Network interconnections are made through the WIA-PA gateway where, in addition to the communications to the WIA-PA NM and SM, the WIA-PA gateway can communicate with other WIA-PA devices to exchange information between the devices. The WIA-PA gateway also is able to connect other networks such as wired fieldbus.
The WIA-PA standard specifies five types of devices including host computer, gateway device, routing device, field device and handheld device, which includes two functions — configuring network devices and monitoring network performance. A WIA-PA handheld device, like other network devices, connects to the WIA-PA network via the gateway device and routing device.
Standards
Because we operate in a global environment and manufacturers want their equipment to be deployable anywhere in the world, it is important that the communications platform — radio — can be used in the target country. Since the 2.4 GHz frequency is the only practical option for global deployment, it is the ISM band being used for all three protocols being developed.
Unfortunately, many other devices such as cellular phones, wireless phones in your home and various other items including remote control cars and toys use the 2.4 GHz frequency. Fortune magazine recently predicted exponential growth of smart phones pushing data transfer into the exabytes (1018 bytes or 1 billion gigabytes)/month range.
This growth in traffic will make the dropped-signal problem worse and will be a factor that standard developers will consider when they release the next version of the protocol. ISA100 with its white-list approach already has taken the first step in rechecking that a channel has become available for use again.
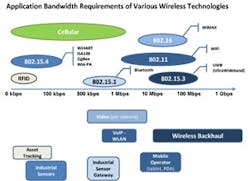
Figure 2: The range of wireless protocols using the ISM bands and associated typical applications reinforces how the demand for these bandwidths will continue to grow.
The range of wireless protocols using the ISM bands and associated typical applications reinforces how the demand for these bandwidths will continue to grow over time, thus putting more demands on the industrial network to provide the necessary real-time process data updates (Figure 2).
The thee organizations developing industrial wireless standards all have plans for adoption by the IEC, and each of them is in different stages in the process.
WirelessHART — The International Electrotechnical Commission (IEC) approved the WirelessHART communication specification (HART 7.1) as a publicly available specification (IEC/PAS 62591Ed. 1) in 2008. The national committees of 29 countries participate in the approval ballot which is presently at the committee draft for vote (CDV) stage and therefore the furthest along the approval process of the three industrial wireless standards planned for consideration by the IEC.
WIA-PA—Its working group started standardization work in 2006, with input gathered from more than 20 companies, institutes and universities in China. On Oct. 31, 2008, WIA-PA passed voting of IEC/SC65C and was published as IEC/PAS 62601 and passed the committee draft (CD) stage on March 5, 2010.
In parallel, this standard has been submitted to the Standardization Administration of China (SAC) and, when approved, it will become a Chinese national standard.
ISA-100—ISA-100.11a-2009 is a published ISA standard approved by the ISA Standards & Practices Board on Sept. 8, 2009. During a further review of the approved document, a use case study indicated that some corrections were needed to ISA-100.11a-2009. A motion to that end successfully passed March 31, 2010, and therefore it does not make sense to submit ISA-100.11a-2009 for ANSI approval when it's clear it needs some corrections. ISA will wait and submit the revision, which will be ISA-100.11a-2010 (or -2011) to ANSI for approval as an American national standard. For now, ISA-100.11a-2009 is an approved ISA standard and will continue to be until the revision now underway is completed. Until such time as the ISA-100 standard is accepted as an ANSI standard, it will not be submitted to the IEC for approval.
Like any installation, wireless is not without its worries. However, the good news is that many of the items of concern are being addressed through the standards development process on which the products being released to market will be based. Industrial wireless might not yet be ready for the mainstream, but it is certainly headed in that direction.
Larry Pereria, Wayne Manges, Peter Fuhr, Charley Robinson of the ISA-100 committee, Ed Ladd from the HART Foundation and Dr. Ding Lu at the Instrumentation Technology & Economy Institute, P.R.China (ITEI) assisted with this article.
About the Author
Ian Verhappen
ISA fellow

Leaders relevant to this article: