What's important to apply RFID technology correctly in applications
Not much draws the attention of industrial people better than discussing the Internet of Things (IoT), machine-to-machine (M2M) and other wireless-technology acronyms such as LoRa (long-range, low-power wireless), 6LoWPAN (Internet Protocol, version 6, low-power wireless personal area network) or BLE (Bluetooth low-energy).
However, to improve the resilience of an industrial process, increase your competitiveness or create new services by digitalizing products, the process to be changed, improved or created should be well understood. The technology comes afterward. Nevertheless, to make the difference between what could be a pure dream or an off-the-shelf solution, it's worth discussing how the technology works, what the ongoing and upcoming capabilities are and how other stakeholders will implement it.
Radio-frequency-identification (RFID) technology is quite old. The trouble is that there are many different technologies behind this simple acronym, and often technology providers only master one of those, so it may be difficult to determine if the proposed solution is a good one. So, let’s go back to basics and take a moment to revisit how RFID works.
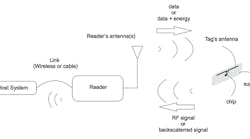
An RFID tag, consisting of an electronic chip connected to an antenna, sends information to an RFID interrogator, often called a reader (Figure 1). The interrogator requires a power source such as a battery or external supply, but what about the RFID tag? The microelectronic chip needs to be powered to operate. In most cases, just adding a power supply to the RFID tag is not the answer. The RFID tag would be too big and expensive, and maintenance of the battery could be difficult. So, the energy is provided by the reader, using radio-frequency (RF) waves each time it wants to communicate with the tag. This is called “tele-supply.”
Figure 1: Main elements of an RFID system include an RFID tag with electronics and antenna and an interrogator with antenna connected to a controller.
Using this RF wave energy, the RFID chip can decode the commands coming from the interrogator and respond to these commands or transmit information without waiting for the interrogator to request it. The way to respond to an interrogator's commands is, like the tele-supply, a characteristic of RFID systems.
Some RFID chips have an embedded radio frequency transmitter capable of generating its own RF signal, called active RFID. This type of transmitter is more complex and costs more. Furthermore, the energy recovered by the remote power supply may not be sufficient to properly power such a transmitter.
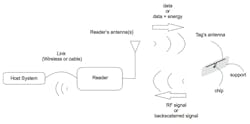
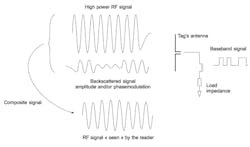
To avoid this complexity while being able to communicate with the interrogator, the RFID tag modifies its own characteristics such as impedance or radar equivalent surface. This will have the effect of modifying the characteristics (amplitude and/or phase) of a signal reflected by the tag toward the interrogator. This technique, called backscattering or load modulation, is the basis for communication of passive RFID tags—RFID chips with no embedded RF transmitter (Figure 2).
Figure 2: Backscattering is a communication technique that optimizes an RFID tag's signal and read range.
RFID is not the only technology for automatic identification and data capture. Barcodes (1D or 2D) and optical character recognition (OCR) are widely used and have the advantage of being, in their simplest forms, relatively inexpensive. However, RFID has advantages over these techniques.
Based on the radiation or propagation of electromagnetic waves, RFID technology doesn’t require optical visibility for tag reading, although metal and some other materials can strongly disrupt this reading, requiring special tags to overcome this issue. Contactless reading is another advantage of using RFID. Depending on the frequencies and tag sizes, the distance to which a tag can be read ranges from a few millimeters to a few meters for passive, batteryless technologies. With a battery and active technology, this distance can exceed 100 meters without difficulty. Another advantage of RFID technology is its ability to read multiple tags simultaneously. For some communication protocols, the interrogator can identify several hundred different labels in a few seconds. A fourth advantage of RFID lies in the fact that this technology is based on a microelectronic chip. Its content is by definition the unique identification number of the object to which the tag will be attached. Depending on the application, this unique identification number may be longer or shorter. The unique item identifier (UII) could be a 96-bit-long serialized global trade identification number (SGTIN) or a 128-bit long global returnable asset identifier (GRAI). Beyond these identifiers, the chip may have a programmable or rewritable memory area enabling the user to access information directly by reading the contents of that memory. It can also add or modify this information during the life of the object. This information can be encrypted, and, with access rights management, several users can share the memory area.
With all these features, a common question when specifying an RFID system is the read distance of an RFID tag. While important, it is only the first of a series of steps where the user will have to decompose its process and sometimes question its principles to take advantage of the best of these technologies.
ALSO READ: Closer to useful RFID
How many RFID technologies are out there?
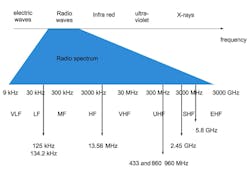
There are different ways to classify RFID. The most common way is to use the frequency at which the system works, which includes low-frequency (LF), high-frequency (HF) and ultra-high-frequency (UHF). Behind these acronyms, there are physical issues. There are two kinds of systems defined by the coupling—the way energy and communication signals are carried by electromagnetic fields—between tags and readers.
The first classification can be summarized by the fact that the coupling between the interrogator and the tags is either mainly magnetic or mainly electric. It is also referred to as near-field communication (NFC) or far-field operation. When operating in an LF or HF range, the wavelength is so large that the distance between the reader and the tag is small compared to this wavelength creating a near-field configuration where a magnetic field is used to couple a reader and tags. In this case, an antenna's main parameters affecting operation are loop size and the number of turns; but, as magnetic fields decrease rapidly, these kinds of systems cannot operate at distances greater than 1 meter.
When operating at higher frequencies, the wavelength decreases, forming more of an electromagnetic field. In this case, antennas are mainly based on a dipole pair, and the impedance matching between the antenna and the RFID chip is the main parameter. As electromagnetic fields decrease less rapidly with distance than pure magnetic fields, the read range of passive, batteryless tags increases to a distance of 10 meters (Figure 3).
Figure 3: There are a wide range of available frequencies for use in RFID applications.
A second possible classification can be made according to whether the RFID tag has an RF transmitter, known as active RFID, or backscatters an RF signal from the interrogator, known as passive RFID. A third classification of the RFID systems can be made according to whether the chip embedded on the label is read-only or that new information can be written, once or several times, via commands transmitted by the interrogator.
Finally, a fourth classification can be made according to the communication protocol between the label and the interrogator. In one case, the tag, once present in the interrogator field, waits for a command from the reader to transmit information. This is called interrogator talk first (ITF) protocol. In other cases, the label transmits information as soon as it is activated by the interrogator’s energy. This is called tag talk first (TTF). Of course, variants of these protocols can be found in various ISO or proprietary standards.
How to choose the best RFID technology for the application
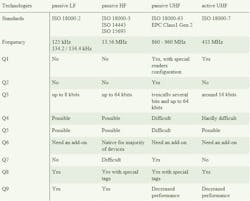
Some common application questions can be sorted to determine which RFID technology is best-suited. There is no one-size-fits-all technology, so the difficult prioritization of capabilities is required to decide between passive LF, passive HF, passive UHF and active UHF. The examples of RFID applications in Table 1 should help when specifying an RFID technology.
Q1: I need to read tags at more than 30 meters (for locating purposes, for example).
Q2: I need to inventory boxes that contain more than 100 tagged items.
Q3: I need to write a lot of information in the memory of the tag (in addition to a unique identifier (UID, EPC, UII)).
Q4: I want a well-defined reading area.
Q5: I want to read stacked tags.
Q6: I want to read tags with a smart phone.
Q7: I want to follow GS1 general specifications.
Q8: I want to trace some metallic items.
Q9: I want to use RFID in a humid or wet environment.
Table 1: There is no one-size-fits-all technology, so the difficult prioritization of capabilities is required to decide between passive LF, passive HF, passive UHF and active UHF.
Traceability of cutting tools
A machine used to produce expensive, application-critical parts has to be automated to:
- select the right cutting tool, based on the material and the shape to be machined
- manage the use of the cutting tools; old cutting tools need to be replaced or revised.
This will reduce human error and work accidents that may cause a system to shut down because a tool either broke during the manufacturing process, was not operating properly due to being worn out or was not installed in the correct location and was thus being used inappropriately. As more machines are computer numerical controlled (CNC), it becomes easy to use RFID technologies to overcome these issues. Automation can be added using an RFID tag, smaller than a fingernail, that is permanently attached or embedded on the cutting tool. An RFID reader is added to the tool carrier that reads the tag ID to confirm every machining program uses the right tool. This solution requires reading one tag at a time at a distance less than a few centimeters. When specifying the RFID technology, the significant amount of metallic parts in such a machine must be considered. Lastly, the RFID tag must not prevent proper functioning of the small tool. LF technology is a good choice to fulfill all of these requirements and widely used in industry.
Tracking goods in a conveyance system
Imagine a conveyance system like those you can find in breweries with beer kegs or in warehouses for logistic purposes. These conveyors are often implemented in harsh environments with a lot of metallic parts and rotating machines. In order to automate the tracking and routing of goods, you need to automatically identify those goods. RFID tags will have to be affixed to the items, but you will also need to place RFID readers along the conveyors. You may of course add some fixed readers and antenna or even tunnels, but this requires space. More and more RFID providers propose solutions that can be easily plugged on existing conveyors together with conveyors from manufacturers that propose RFID-ready solutions. Another way to implement RFID could be to directly add readers to an existing machine that already serves another purpose on the conveyor line, such as pallet handlers. Depending on the requirements—for example, number of tags to be read simultaneously or the density of conveyors—you may choose either HF or UHF technology. Today, the trend is clearly to use UHF, whatever the environment, simply because the majority of items are UHF-labeled.
Traceability of tools and other manufacturing devices within a facility
How much time is lost by workers searching for the right tool for a task? Searching for tools reduces efficiency, and sometimes workers may use an inappropriate tool, risking injury. Add to this the fact that some tools have to be revised or calibrated regularly, and this could be a nightmare for the managers. Adding RFID to a tool enables interrogation of a database to determine the location, the number of times used, the purpose of use and who used it last. Every tool has its RFID tag to identify it. Combined with a smart cabinet, the solution allows real-time inventory of available tools.
Each time a worker has a defined task, he first interrogates the smart cabinets to find the required tools. To open the cabinet, an employee badge identifies the worker. Once opened, the worker takes all the tools needed. Closing the cabinet’s doors starts an inventory of the contents. Thus, the solution will know who borrows which tools and will be able to give information to other workers, managers and tool providers. Inventory of the cabinet's contents requires the simultaneous read of all the tags. Furthermore, the tools may be returned to different locations in the cabinet. The best solution is to use UHF passive RFID, but because the tools are often made of metal, the RFID tag has to be wisely chosen.
Access control
To manage access to a machine, a production line or a room, identification and possibly authentication of the person is required. Whether the technology used is RFID, fingerprints, magnetic stripe cards or hardware keys, it must be secure and reliable. It is also important to only read the tag when an employee requests access, so the read range should be limited to less than a few centimeters from the reader. That’s why HF RFID is widely used in this application. Of course, there are proprietary solutions based on LF RFID, but they are more and more replaced by HF ones.
Another reason why HF is preferred is the deployment of near-field communication (NFC) technology. Smart phones can read or emulate an HF tag, enabling smarter management of access rights. Granting access to someone for just one day and for a given time slot is an example. To enable this feature, a manager sends a secure, encrypted message to the individual’s smart phone. The person’s smart phone will then be able to emulate an RFID tag to access the building. A car rental company can provide the same feature. If the rental office is closed due to a late arrival, the code can be used to open a car that has an NFC-enabled lock.
Outdoor location of high-value items
Building a fence and hiring security to guard an industrial facility is an option, but as new projects start at different locations, new security problems will occur. One solution could be to tag items with long-range RDID devices and create a radio fence to detect every movement of the tagged items. Whatever the type of site, the tag readers can be configured to cover a defined geographic zone. This solution can detect a theft attempt if the tagged item disappears from the reader’s radar and can locate items on the site.
To cover wide areas with a few readers, active RFID tags are required. This requires monitoring of the active tags' batteries. Fortunately, active tags are smart enough to automatically send information to the readers when battery life decreases. Implementing an equivalent solution with LF of HF passive tags would require security gates with RFID readers and installation of fences around the site. Using UHF passive technology would require the installation of too many readers, but could be utilized for tracking items in a limited area such as inside a building.
e-Kanban
RFID technologies can be mixed to create a custom solution. Let’s take the example of an e-kanban. A kanban system allows demand forecasting, as all necessary parts are refilled automatically. The supply chain of complex assembly systems can be automated using RFID solutions.
In a classic kanban system, every time a bin is emptied an operator removes the box identifier, such as a plastic card with the box number or item identifier, and places it in a dedicated tray or slot. The person in charge of the supply chain collects the cards and orders all of the needed items.
The first step would be to replace the card with a passive RFID tag. An RFID reader would be used to read the tags, and reordering would happen automatically without error or omission. Additionally, an active tag can be linked to the passive one. Every time an operator removes the active tag, it sends information wirelessly to the server. This information is the ID of the passive tag. As this ID is linked to the content of the box, the server can decode the signal and prepare an order automatically. For the operator, nothing changes. When a box is empty, he removes the active tag and puts it in the tray. Once the box is full again, the operator attaches any active tag back to the bin. This active tag will read the ID of the passive tag and send it when detached.
RFID as a pure communication protocol
RFID is not only made for identification purposes. It could be used to transfer information between devices. RFID chips can be connected to sensors such as in battery-assisted passive (BAP) RFID tag applications, but it can also have an inter-integrated (I2C) bus connected to a more complex electronic system.
Let’s take the example of an electrical switching box. Adding monitoring of switching devices could become difficult due to the interface needed including the programming, navigation buttons and LCD screen. Furthermore, such an interface adds cost and hardware to the electrical switching box. Instead, an NFC tag, as small as a fingernail, could be added to the switching device. It could provide the ability to send and receive information to a smart phone by developing a simple and efficient HMI to set parameters or monitor the switching device. Once all parameters are set up, the smart phone is tapped on the NFC tag, which triggers all parameters to automatically transfer to the switch box. Tapping the smart phone to the NFC tag also allows collection of tag information automatically. In this example, the NFC tag is used as a contactless communication protocol with a 106 kbit/s data rate.
In conclusion, RFID options are increasingly diverse. A few years ago, there were few choices. Today, the tag size decreases together with the increase of performances. Multiple packaging is available for harsh environments. Tags can be put directly on metal and can survive to temperatures up to 250 °C. With UHF passive RFID, you can read up to 400 tags/s. RFID will no more walk alone, and adding sensors has become commonplace, helping operators to implement qualitative traceability. Choosing the right technology could become a nightmare if the good questions are not asked at the right time. When thinking about a new project or service, RFID by design has to be the main thrust because adding the RFID, even if this is the right technology, to an existing product is always more difficult.
Claude Tételin is chief technical and operation officer at National Reference Center RFID in Rousset, France. Contact him at [email protected].
Sponsored Recommendations
Latest from RFID

Leaders relevant to this article: